Protect Your Business With PenTests
A PenTest simulates a cyberattack to assess your security environment. It prioritizes vulnerabilities by degree of risk, addressing critical issues first and exposing vulnerabilities for potential entry points. Learn more here.
PenTests are 100% independently performed by certified Kaseya OSP, CISSP, CEH, and OSCE certified experts with 10+ years of experience. Kaseya is trusted globally to manage and secure more than 300 million devices.
Stop over 99.9% of hackers.
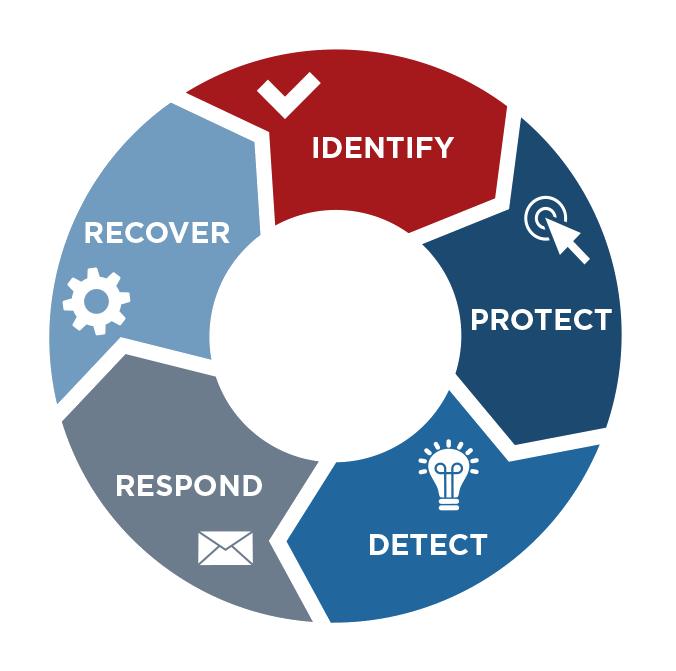
Here’s what we know: The number of cyber threats are at an all-time high. Many organizations assume they are protected from cyber threats, but the reality is they are not. PCA has insight and access to tools that take just minutes to get you started. Your cybersecurity strategy should have a layered approach to protect all areas and data in your business. PCA follows the CIS controls, a subset of the NIST Cybersecurity Framework.
Don’t know where to start when it comes to identifying your cybersecurity posture? PCA creates tools like this self-assessment that will help you get the visibility you need and we are here to help clarify or walk through it with you.
Common Features
- Business continuity
- Disaster recovery
- Critical infrastructure
- Network / Cloud security
- Application security
Common Benefits
- 24/7/365 network protection
- Proper protocols in place
- Defense to the rise of hackers
- Minimal chances for data breach
- Peace of mind
Multi-Factor Authentication FREE 60-Day Trial
It’s quick and easy and we just want to eliminate your company’s #1 risk right off the bat. With this MFA tool, you will immediately bridge the security gaps that leave your company vulnerable to a breach.

Cybersecurity Awareness Training
One of the biggest risks begins with your people and their level of awareness and understanding. We can educate your users with our PCA-developed Cybersecurity Training.
- Develop a security awareness program
- Regularly educate your employees
- Learn about latest cybercriminal techniques
- Mitigate the gaps in your protection
- Refresh policies and remain compliant
- Identify vulnerabilities and act before disaster
